Download latest version
| Name | Version | md5sum | Date |
|---|---|---|---|
| oclHashcat for AMD | v1.20 | c68ab6ca795d71cf4de429af7bdc6234 | 2014.04.26 |
| oclHashcat for NVidia | v1.20 | 4da2b50410c1dbb8454dedfd632d4049 | 2014.04.26 |
GPU Driver requirements:
- NV users require ForceWare 331.67 or later
- AMD users require Catalyst 14.4 or later
Features
- Worlds fastest password cracker
- Worlds first and only GPGPU based rule engine
- Free
- Multi-GPU (up to 128 gpus)
- Multi-Hash (up to 100 million hashes)
- Multi-OS (Linux & Windows native binaries)
- Multi-Platform (OpenCL & CUDA support)
- Multi-Algo (see below)
- Low resource utilization, you can still watch movies or play games while cracking
- Focuses highly iterated modern hashes
- Focuses dictionary based attacks
- Supports distributed cracking
- Supports pause / resume while cracking
- Supports sessions
- Supports restore
- Supports reading words from file
- Supports reading words from stdin
- Supports hex-salt
- Supports hex-charset
- Built-in benchmarking system
- Integrated thermal watchdog
- 100+ Algorithms implemented with performance in mind
- ... and much more
oclHashcat Screenshot
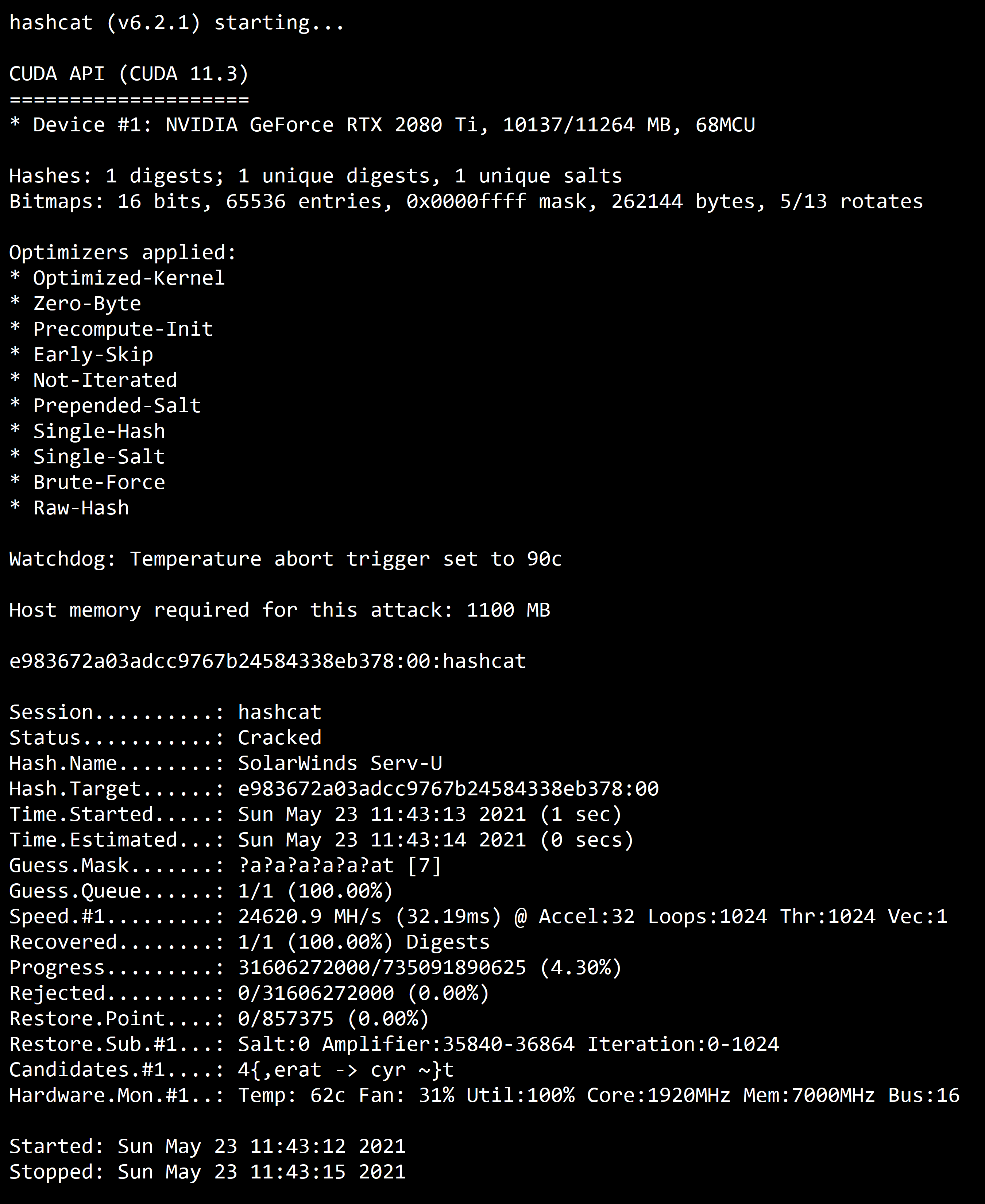
Attack-Modes
- Straight *
- Combination
- Brute-force
- Hybrid dict + mask
- Hybrid mask + dict
* accept Rules
Algorithms
- MD4
- MD5
- SHA1
- SHA-256
- SHA-512
- SHA-3 (Keccak)
- RipeMD160
- Whirlpool
- GOST R 34.11-94
- HMAC-MD5 (key = $pass)
- HMAC-MD5 (key = $salt)
- HMAC-SHA1 (key = $pass)
- HMAC-SHA1 (key = $salt)
- HMAC-SHA256 (key = $pass)
- HMAC-SHA256 (key = $salt)
- HMAC-SHA512 (key = $pass)
- HMAC-SHA512 (key = $salt)
- LM
- NTLM
- DCC
- DCC2
- NetNTLMv1
- NetNTLMv1 + ESS
- NetNTLMv2
- Kerberos 5 AS-REQ Pre-Auth etype 23
- AIX {smd5}
- AIX {ssha1}
- AIX {ssha256}
- AIX {ssha512}
- FreeBSD MD5
- OpenBSD Blowfish
- descrypt
- md5crypt
- bcrypt
- sha256crypt
- sha512crypt
- DES(Unix)
- MD5(Unix)
- SHA256(Unix)
- SHA512(Unix)
- OSX v10.4
- OSX v10.5
- OSX v10.6
- OSX v10.7
- OSX v10.8
- OSX v10.9
- Cisco-ASA
- Cisco-IOS
- Cisco-PIX
- GRUB 2
- Juniper Netscreen/SSG (ScreenOS)
- RACF
- Samsung Android Password/PIN
- MSSQL
- MySQL
- Oracle
- Postgres
- Sybase
- DNSSEC (NSEC3)
- IKE-PSK
- IPMI2 RAKP
- iSCSI CHAP
- WPA
- WPA2
- 1Password, cloudkeychain
- 1Password, agilekeychain
- Lastpass
- Password Safe SHA-256
- TrueCrypt 5.0+ PBKDF2 HMAC-RipeMD160 + AES
- TrueCrypt 5.0+ PBKDF2 HMAC-SHA512 + AES
- TrueCrypt 5.0+ PBKDF2 HMAC-Whirlpool + AES
- TrueCrypt 5.0+ PBKDF2 HMAC-RipeMD160 + AES + boot-mode
- TrueCrypt 5.0+ PBKDF2 HMAC-RipeMD160 + AES + hidden-volume
- TrueCrypt 5.0+ PBKDF2 HMAC-SHA512 + AES + hidden-volume
- TrueCrypt 5.0+ PBKDF2 HMAC-Whirlpool + AES + hidden-volume
- TrueCrypt 5.0+ PBKDF2 HMAC-RipeMD160 + AES + hidden-volume + boot-mode
- SAP CODVN B (BCODE)
- SAP CODVN F/G (PASSCODE)
- Citrix Netscaler
- Netscape LDAP SHA/SSHA
- Apache MD5-APR
- hMailServer
- EPiServer
- Drupal
- IPB
- Joomla
- MyBB
- osCommerce
- Redmine
- SMF
- vBulletin
- Woltlab Burning Board
- xt:Commerce
- Wordpress
- phpBB3
- Half MD5 (left, mid, right)
- Double MD5
- Double SHA1
- md5($pass.$salt)
- md5($salt.$pass)
- md5(unicode($pass).$salt)
- md5($salt.unicode($pass))
- md5(sha1($pass))
- sha1($pass.$salt)
- sha1($salt.$pass)
- sha1(unicode($pass).$salt)
- sha1($salt.unicode($pass))
- sha1(md5($pass))
- sha256($pass.$salt)
- sha256($salt.$pass)
- sha256(unicode($pass).$salt)
- sha256($salt.unicode($pass))
- sha512($pass.$salt)
- sha512($salt.$pass)
- sha512(unicode($pass).$salt)
- sha512($salt.unicode($pass))
Tested OS
- All Windows and Linux versions should work on both 32 and 64 bit
Tested GPU
- All CUDA and Stream enabled cards should work
Performance
- PC1: Ubuntu 13.04, 64 bit
- Catalyst 13.11b
- 1x AMD hd7970
- stock core clock
- PC2: Windows 7, 64 bit
- ForceWare 325.15
- 1x NVidia gtx580
- stock core clock
- PC3: Ubuntu 12.04.3, 64 bit
- Catalyst 13.11b
- 1x AMD hd6990
- stock core clock
- PC4: Ubuntu 12.04.3, 64 bit
- ForceWare 319.37
- 1x NVidia gtx560Ti
- stock core clock
- PC5: Ubuntu 12.04.3, 64 bit
- Catalyst 13.12
- 8x AMD R9 290X
- stock core clock
| Hash Type | PC1 | PC2 | PC3 | PC4 | PC5 |
|---|---|---|---|---|---|
| MD4 | 16116M c/s | 4082M c/s | 20853M c/s | 3224M c/s | 162777M c/s |
| MD5 | 8089M c/s | 2414M c/s | 10742M c/s | 1838M c/s | 81549M c/s |
| SHA1 | 2510M c/s | 710M c/s | 3809M c/s | 591M c/s | 27333M c/s |
| SHA256 | 1032M c/s | 347M c/s | 1479M c/s | 231M c/s | 11231M c/s |
| SHA512 | 74M c/s | 114M c/s | 217M c/s | 70M c/s | 797M c/s |
| SHA-3(Keccak) | 142M c/s | 94M c/s | 175M c/s | 59M c/s | 1714M c/s |
| RipeMD160 | 1678M c/s | 560M c/s | 2280M c/s | 394M c/s | 17498M c/s |
| Whirlpool | 31M c/s | 94M c/s | 88M c/s | 45M c/s | 363M c/s |
| LM | 1285M c/s | 475M c/s | 1070M c/s | 251M c/s | 10704M c/s |
| NTLM | 15514M c/s | 3905M c/s | 20109M c/s | 2807M c/s | 140965M c/s |
| NetNTLMv1 | 8018M c/s | 1889M c/s | 9786M c/s | 1306M c/s | 73324M c/s |
| NetNTLMv2 | 555M c/s | 182M c/s | 510M c/s | 103M c/s | 6297M c/s |
| WPA/WPA2 | 131k c/s | 45k c/s | 178k c/s | 32k c/s | 1336k c/s |
For example, PC5 can do 140965M c/s against NTLM, that is 140965000000 tries per second.
Help
A detailed description of all commandline parameters is available by using --help. Next to that, the rar-package contains extensive documentation. Look for examples.txt. If you encounter a Bug, report it in the Forums where Fixes and Beta versions are announced as well.
Download older version(s)
This is a list of older oclHashcat versions, it's not always bad to grab the latest version.
| Name | Version | md5sum | Date |
|---|---|---|---|
| oclHashcat | v1.01 | 6dcc0e5107c3a7fc4b5013e032829d70 | 2014.01.01 |
| oclHashcat | v1.00 | ebc755aa513cab75eae5603d3fc204bf | 2013.12.06 |

No comments:
Post a Comment